28 Years of Winning Cases
About Dos and DDoS Attacks
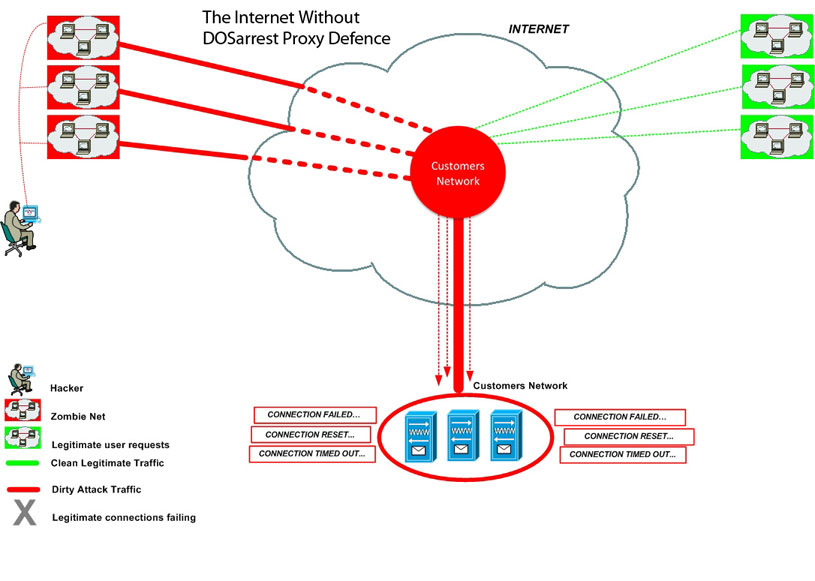
A DoS attack, or Denial of Service attack, is when an enormous amount of “junk” traffic is forced on to a targeted web server by a hacker, or hackers, to achieve such overcapacity that legitimate traffic is denied access to the site, which is a real nightmare scenario for any orginazation or business. While a successful DoS attack can be orchestrated and executed with very few computer systems, Distributed Denial of Service attacks (DDoS) raise the bar considerably by magnifying the effect exponentially. DDoS attacks typically leverage large botnets, which can consist of thousands, if not millions of zombie systems, which are essentially previously compromised systems under hacker control, usually without the user of the compromised system ever even knowing their system was involved. Unfortunately, with the prevalence today of hacker black markets, hackers and spammers not only rent out the use of massive botnets to anyone willing to pay the price, there is also software available which can allow even a single individual to leverage all that computing power to launch very successful and devastating DDoS attacks against their chosen target.
GDF DDoS Protection
Global Digital Forensics has partnered with DOSarrest to offer a robust, yet affordable, security offering. DDOS protection in a cloud based "instant on" offering gives our clients the final crucial brick in the defensive wall. Now GDF clients can remediate DDoS attacks (Distributed Denial of Service) in near real time and get unparalleled insight into the traffic attacking their network through the GDF Security Portal.
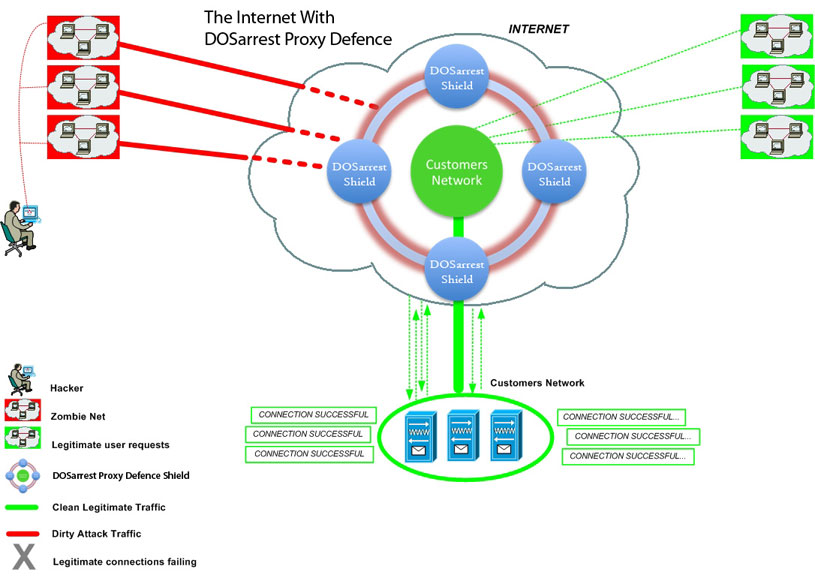
DOSarrest is a cloud based DDoS protection service that, since its inception in 2007, has developed, implemented and real-world tested a wide range of proprietary methods and techniques to stop DDoS attacks. We do not rely on purpose-built DDoS mitigation devices to stop all attacks. Our experience has taught us that no one DDOS mitigation device can stop all varieties of DDoS attacks in existence today.
DDoS Protection Installation and Maintenance
Our Nodes are geographically dispersed in such a way as to offer our worldwide customer base, not only DDoS protection, but also able to handle large bursts of legitimate traffic. It operates like a content delivery network, except it can stop any and all DDoS attacks. We cache, as well as proxy, for added performance.
Once a website is running on our service, the site is protected 24/7 from any DDoS attack. We set alerts on the number of requests to your site for a given unit of time, using a baseline for what is normal for your site. Should the requests exceed the predetermined threshold, our team will investigate to determine the next course of action and apply any necessary mitigation techniques. This is all performed without interruption in service, or intervention by the customer. We have also built our own custom monitoring system that will alert us to any performance or site unavailability. This custom system is completely external to any of our traffic scrubbing nodes, from 6 different networks, in 3 geographic regions, that constantly monitors your site being anycasted from all of our nodes.
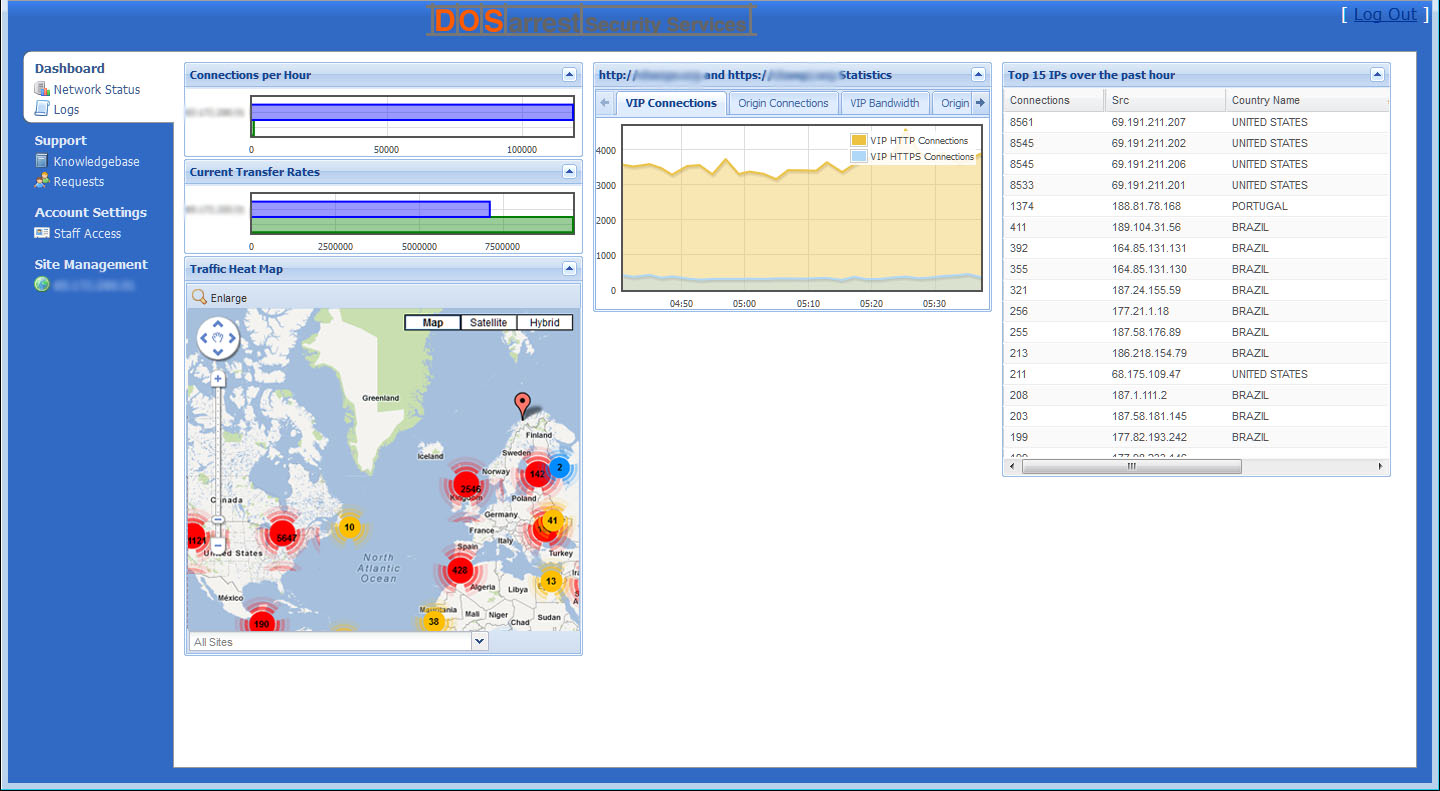
We have our own custom built customer access area (DSS) where customers are able to view and make changes to their configurations, as well as see any attack in real-time.
Customers are able to customize the cache for optimal performance and can fine-tune hundreds of parameters, to enhance security or improve performance.
All of the above is supported 24/7 by an experienced DDOS mitigation team.
So don’t let the success of your organization be compromised by the whims of hacktivists, disgruntled employees, or competitors. Professional protection is just a phone call away.